
Increasing Security And Resilience Of Critical Infrastructure Networks With The New 1588-2019 Security Standard
Status of Precision Time Protocol (PTP) Standards
Precision Timing Protocol (PTP) is a protocol used to synchronize clocks in many critical infrastructure networks such as telecommunication, energy, utilities, transportation and other industries. An important aspect of these crucial networks is that they need to be secure. So the question is, should PTP also be secure – and if so, what are the essentials operators must know to effectively maintain service continuity?
PTP has been used for many years to synchronize clocks based on the assumption that critical infrastructure networks are mostly closed environments, thus less vulnerable to attacks. However, with more focus and awareness today about security across multiple industries, addressing security to protect timing – and more specifically, packetbased timing such as PTP 1588 – has become a much more prominent priority.
In the latest release of the PTP standard IEEE® 1588-2019 (version 2.1), four new security prongs or concepts were introduced to address security and resiliency. These prongs can be used individually or in combination to protect against security attacks.
This paper presents a brief introduction on the four security prongs and addresses the reasons why Prong C and Prong D are key priorities to address PTP security now, while also recognizing the need for authentication or encryption in the longer term.
Integrated Security Mechanism – Prong A
In Prong A, a new Authentication Type-Length-Value (TLV), a normative TLV, was added at the end of PTP messages to ensure the integrity and authenticity of the messages.
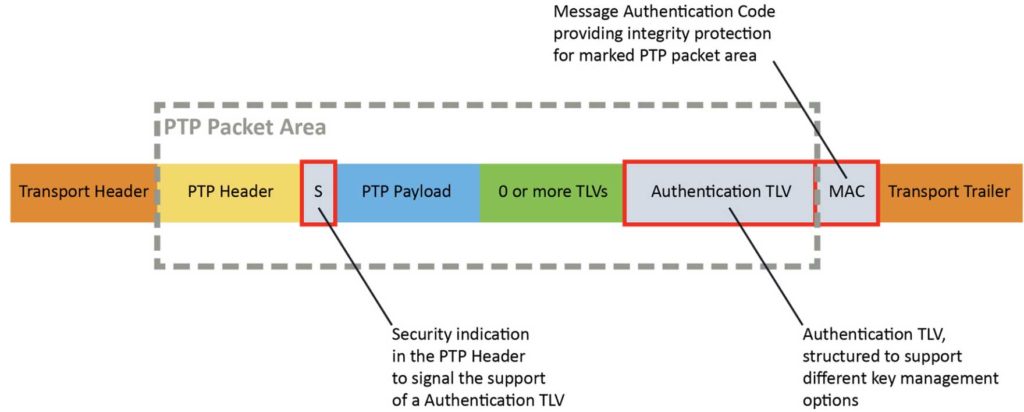
Figure 1-1 shows a 1588 PTP packet with various fields and the specific Authentication TLV appended right ahead of the Message Authentication Code. Right after the PTP header a field (“S”) indicates the Authentication TLV is used in this packet.
Since PTP messages do not carry sensitive information and nothing confidential in timestamps, the integrity and authenticity of the PTP messages are what is important. Integrity ensures the packets were not changed, maliciously or accidentally, along the path. That is why authentication is considered secure without the need for encryption, since PTP information is not confidential.
The security key distribution for the Authentication TLV has not been finalized yet. Currently, proposals are being discussed and reviewed by the Internet Engineering Task Force (IETF) and Institute of Electrical and Electronics Engineers (IEEE).
For this reason, while the authentication of timing packets is a very valuable security enhancement, this capability is probably best implemented once the key distribution is finalized. Therefore, the focus of this paper will not be on this capability, pending further progress in the standards bodies or adoption of authentication keys in PTP clients.
External Security Mechanisms – Prong B
This prong encompasses using well known transport security mechanisms such as IPsec (IP Security) and MACsec (Media Access Control Security) for securing PTP and basically, using existing security infrastructures that may already have been deployed in a network to secure the transport of PTP messages.
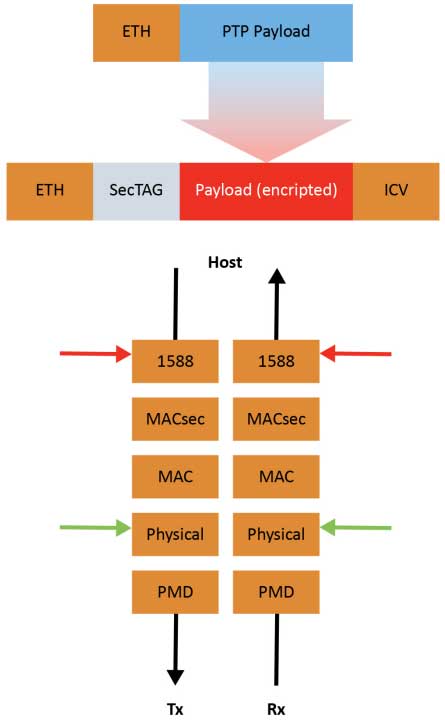
Figure 1-2 shows an encrypted payload preceded by a security TAG field as well as a MACsec layer, both on transmit and receive sides, inserted between the MAC layer and the 1588 layer.
While this approach may sound effective, it is worth noting that because of the added layer of encrypting of PTP packets, the accuracy of the timestamps may degrade, causing it to be outside of the required specifications for some applications. Also, the definition of the timestamp mark is the first byte after the Start of Header (SOH). Prepending data moves, the timestamp is relative to the receiver and requires additional complexity to correct. Application accuracy requirements vary widely and can range from a few nanoseconds in applications such as 5G to milliseconds in a company enterprise network where the primary use case is to synchronize PCs for logging and accounting purposes. These challenges will be discussed later in this paper, along with steps to address them.
The main hurdle to encryption is the requirement to adapt hardware to include a PHY (physical layer of the OSI model) chip that embeds MACsec capabilities. Discussed here also will be the benefits presented by this form of security.
In the short term, however, the assumption will be that operators do not wish to invest in new hardware that supports new PHYs – therefore, the focus here will concentrate on other aspects that can be addressed with today’s timing appliances.
IPsec is a secure network protocol suite that authenticates and encrypts packets to provide secure communication between two devices. IPsec is a layer 3 OSI model scheme, it typically processes authentication and encryption of packets in software which adds a lot of variability to the accuracy of timestamps. It somewhat diminishes the value of PTP being so accurate using hardware timestamping.
Architecture Guidance – Prong C
The architecture that Prong C proposes is a set of methods describing three approaches of securing PTP via resiliency.
Multiple Inputs Using Various Timing Systems
There are other types of timing systems that can be used to complement PTP. Examples include the Global Navigation Satellite System (GNSS), Inter-Range Instrumentation Group (IRIG), and Time-of-Day (ToD), as defined in the ITU G.8271 standard. A timing appliance can test the performance of PTP against other available timing systems to detect timing errors. Having three or more timing systems as potential inputs, the timing appliance can run a majority vote scheme to detect spoofing or delay attacks on the PTP timing system.
A priority scheme can also be used to assign a higher priority value to the more trusted timing systems in the case of a tie when having an even number of timing systems.
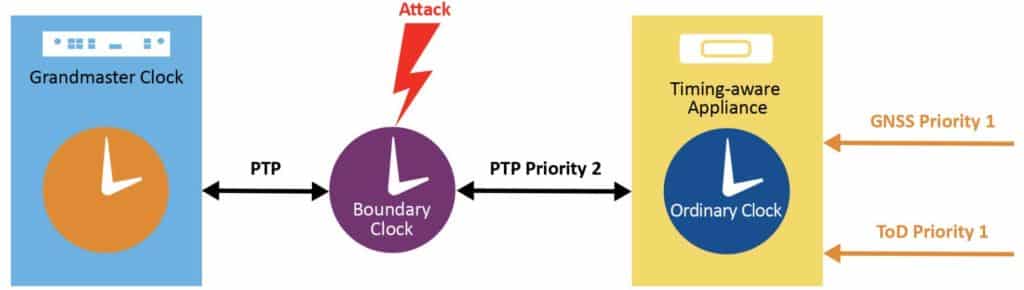
Figure 1-3 shows a timing appliance with multiple timing references, with Priority 1 assigned to GNSS and ToD while Priority 2 is assigned to PTP. If the PTP timing reference path gets compromised, the timing appliance can reject it and use an alternate timing references.
Multiple PTP Grandmasters
Multiple grandmasters can also be used to increase robustness and resiliency against security attacks. In this case, multiple domains and/or multiple profiles can be used to run a majority voting algorithm between multiple PTP instances to detect timing errors.
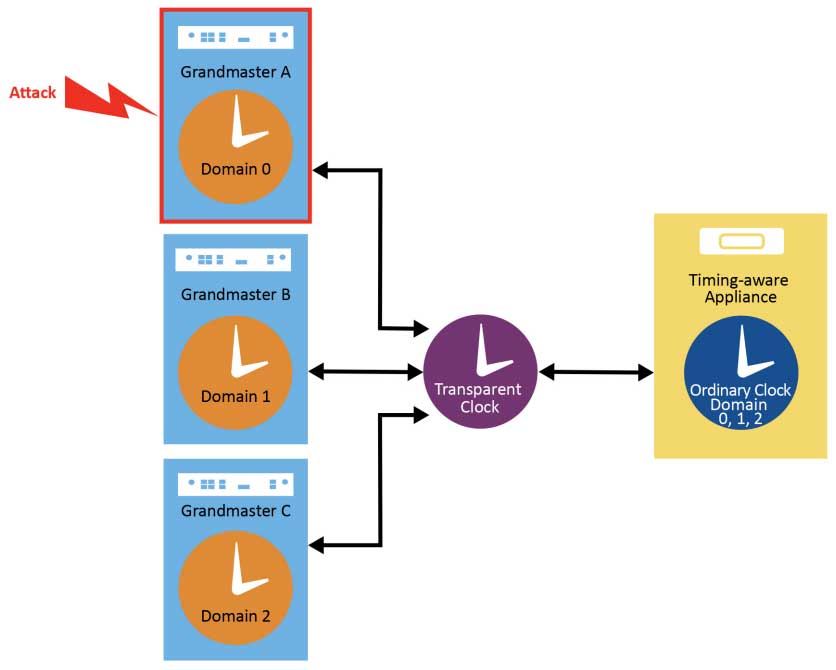
Figure 1-4 shows a timing appliance receiving PTP messages from three separate grandmasters using different PTP domain numbers. If grandmaster A was spoofed, the timing appliance should be able to detect that the timing from grandmaster A does not match the timing coming from grandmasters B and C. In this case, it disqualifies grandmaster A as a timing reference and potentially raises an alarm to the Network Management System (NMS), so a network engineer can investigate and take appropriate action.
Multiple Network Paths
This method describes the use of multiple paths to the timing appliance. A single multi-port grandmaster or multiple grandmasters can be used in this case. If a timing appliance supports multiple physical ports capable of running PTP, then it can compare the timing performance on the paths and run a majority voting algorithm to detect anomalies. The timing appliance can detect large time jumps or unexpected path delay on the path by comparing the timing performance against the other paths.
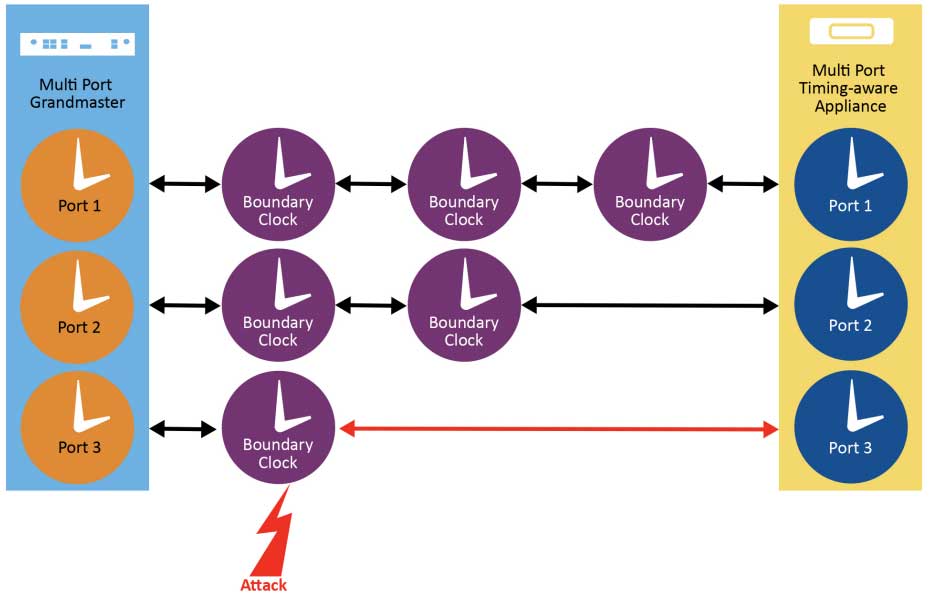
Figure 1-5 describes a multi-port grandmaster connected to a multi-port timing appliance via three different paths, one with three boundary clocks (BCs), one with two boundary clocks and one with a single boundary clock. The standard would select the path with the lower number of BCs. We will show in this document that specific implementation can provide more value than the standard by taking into account other factors than simply the number of BCs on the respective paths.
Monitoring and Management – Prong D
In Prong D, signal monitoring and external management mechanisms can be used to detect time anomalies. Typically, this security approach has more value when it is combined with the architecture security prong, as it feeds very well into the majority voting algorithm to qualify or disqualify a timing system.
Various parameters and aspects could be monitored to enhance security, including factors like link delay, unexpected offset jumps, or large variations in asymmetry between the Sync T1/T2 timestamps and Delay T3/T4 timestamps.
Additional parameters such as counters that can check the PTP message rate or detection of duplicate PTP messages using sequence ID could also provide some indication of possible DoS or replay attacks.
An external Network Management System (NMS) has a higher view of the network topology and can monitor all devices and network changes. Upon detection of an attack on grandmaster or path, it can inform a timing appliance to stop using the grandmaster or path for time synchronization.
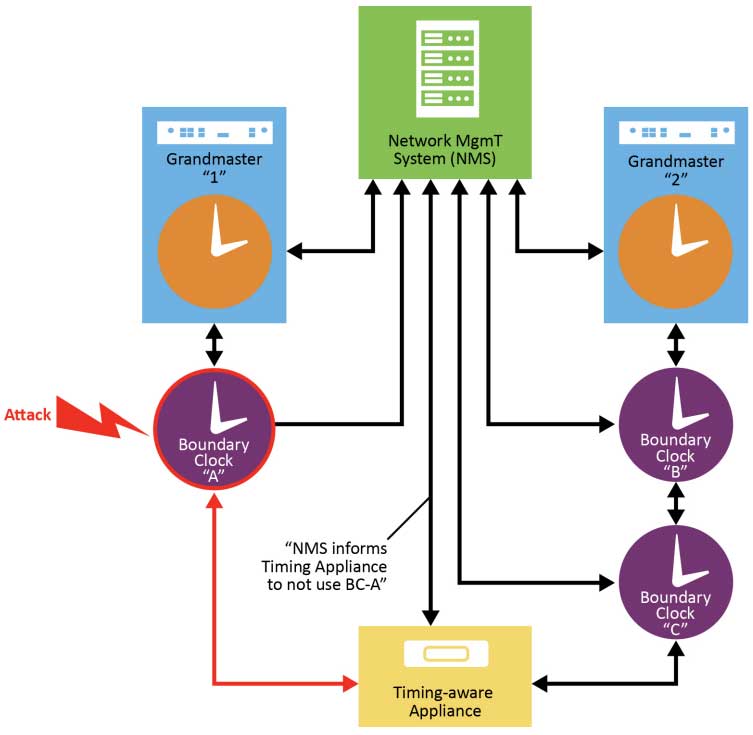
NMS detects that BC-A was attacked so it informs the Timing Appliance not to synchronize to BC-A, instead use sync from BC-C
Recommendations to Secure PTP Today
Authentication and Encryption
Critical infrastructure networks are closed and protected environments less prone to typical attacks than networks that are more open in nature. Typically, access control mechanisms are very much needed to secure the connectivity to the various timing devices in the network.
Firewalls should be the critical first step. Implementing Authentication, Authorization, Accounting (AAA) mechanisms using servers deployed for the purpose of network security such as TACACS+ or Radius are of great value.
The addition of two-factor authentication (2FA) and security levels to categorize users and respective rights also are recommended steps.
However, authentication of PTP traffic per se (Prong A) is a capability to keep in mind but may not be urgent to deploy now, given the lack of finalization at the standard bodies on the topic of key exchange.
Encryption used to be a hurdle as it relates to PTP, for performance reasons. However, today PHY chips not only embed MACsec encryption but also implement mitigation steps to alleviate the performance drawbacks. Therefore, it is recommended that operators move forward with adoption of encryption of PTP (Prong B) for devices now in the design stage and those in which a future-proof evolution is planned.
Security and Resiliency
Prong C and Prong D have introduced security approaches that offer security benefits that can be leveraged to ensure the enablement of more resilient networks.
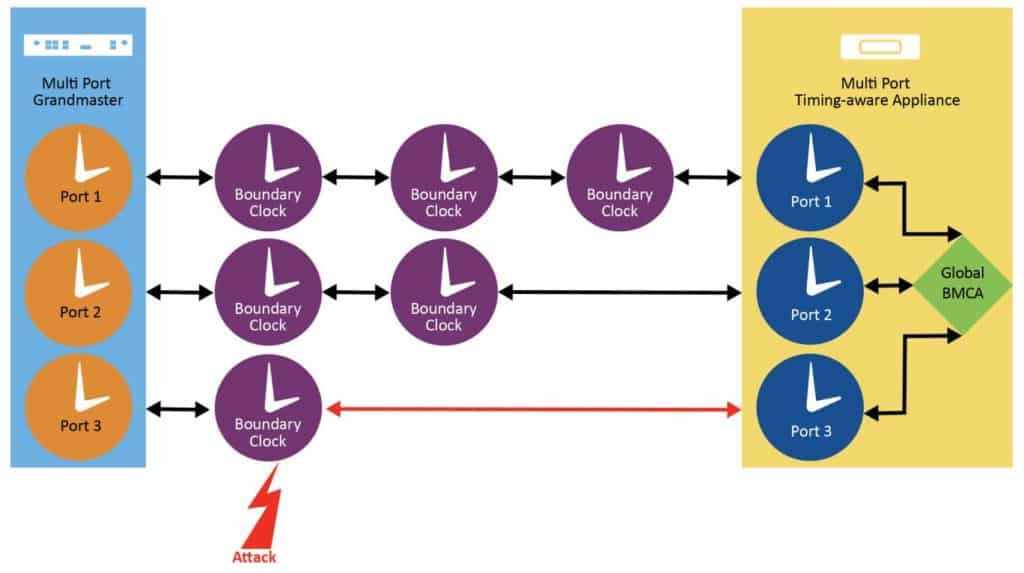
Prong C referred to “majority vote” mechanisms to select the best clock. This majority vote algorithm is defined by the IEEE 1588-2019 standard and involves a Global-Best Master Clock Algorithm (G-BMCA).
Introduction of Global Best Master Clock Algorithm G-BMCA
The Best Master Clock Algorithm (BMCA) is what PTP uses to select the best clock to use as a reference. In the case of a single grandmaster, the BMCA works by selecting the best path from the grandmaster by choosing a path with the least number of boundary clocks, irrespective of the presence of transparent clocks in the path or the path characteristics like jitter, asymmetry and path delay.
G-BMCA was introduced to include path performance and support datasets from multiple PTP instances. The G-BMCA runs as a single instance and uses a Performance Figure of Merit (PFOM) metric calculated in the PTP instance. The PFOM check can be added at any stage in the BMCA datasets comparison tree depending on the confidence level in the metric. Along with datasets from the multiple PTP instances, the G-BMCA decides the best PTP instance that ultimately is used as the reference to the timing appliance.
It is important to note that Prong C and Prong D were defined for security purposes but can be used to provide more resiliency, by providing a more robust Assisted Partial Timing Support (APTS).
Combined with the ability to support three PTP client inputs and the use of G-BMCA, a grandmaster can leverage three other connected grandmasters in the network and select the best to use for APTS when its GNSS connection is poor, spoofed, jammed or otherwise unavailable.
This enables operators to be confident about the robustness and performance of their critical infrastructure network so GNSS can be backed up by PTP in an intelligent, secure and performant manner.
Using not only the number of BCs in the path as the standard defines but also the characteristics of the links in a broader sense shows the value of embedded algorithms in grandmasters offering capabilities beyond the pure definition of IEEE 1588-2019.
Conclusion – Taking the Appropriate Steps to Timing Security
Security has become essential. Securing the timing infrastructure also is a necessity. The four security prongs analyzed in this paper each have strengths and weaknesses. For example, delay attacks cannot be easily detected by the authentication and encryption mechanisms proposed in Prong A and Prong B. Also, some timing appliances lack the complicated hardware of having multiple ports or even the capability of running multiple PTP instances as outlined in the architecture prong.
Microchip Technology continues to invest in supporting the architecture and monitoring, Prong C and Prong D, respectively, as the first phase of addressing PTP security. These architecture and monitoring mechanisms can be easily deployed in existing networks. Similar mechanisms exist today in many telecommunication networks like Virtual Router Redundancy Protocol (VRRP) and can support the adoption of architecture and monitoring of PTP. These capabilities are at the core of Microchip’s new 2.3 software version of TimeProvider 4100, which also supports many other security measures highlighted in this paper, beyond those defined by the four prongs of IEEE 1588-2019.
Microchip offers PHY solutions that support MACsec, enabling critical performance which will be considered for new devices
Contact your local VMA field engineer today if you need help or have any additional questions about Microchip products.









